Files can be safely shared with trading partners, users, clients, and vendors while avoiding having critical documents or files stored, even temporarily, in your DMZ.
But what is this DMZ and what is it used for?
That’s what we’re going to find out in this article.
What is the DMZ and how it works?
The DMZ is the neutral network that resides between the Internet and your organisation’s private network. It’s protected with a front-end firewall that limits Internet traffic to certain systems within its zone. On the back end, an additional firewall resides to prevent unauthorised access from the DMZ into the private network.
The DMZ essentially serves as a staging area between an organisation’s private network and the Internet.
In order to share a document with a trading partner accurately, an internal program or employee would need to first copy the desired file from their private network onto a server in the DMZ. The partner could then download the file from that server using an approved protocol, such as FTP/FTPS, SFTP, or HTTP/HTTPS.
When trading partners need to share documents with an organisation, they would upload the files to a server in the DMZ. Subsequently, an internal program or employee would then scan for the files on the server and pull them into their private network.
How can the DMZ be dangerous and impact security?
Although many organisations exchange files using the DMZ, staging files in a vulnerable location like the very publicly accessible DMZ makes them susceptible to a variety of dangerous attacks from enemy territory.
The DMZ can have a major impact on security if not protected properly. In the event that a hacker gains entry to a file server in the DMZ, they may be able to access and download sensitive data and trading partner files that were placed there. Even encrypted files can be at risk to high-grade attackers if keys or passwords are compromised. There’s also a strong likelihood that any user credentials, certificates, or whatever else is needed for authentication could be maintained in the DMZ, increasing vulnerability.
Also at risk is the file sharing software itself, particularly if it can be accessed from within the DMZ. For instance, let’s say a malicious attacker gains access to your territory by creating a “back door” user account into an SFTP server through its admin console. This user account could seemingly appear as “legitimate” and allow the hacker the opportunity to steal sensitive data files. Audit logs could also be manipulated if they’re stored in the DMZ, allowing the attacker to erase any trail they were ever there.
Secure your DMZ with GoAnywhere Gateway
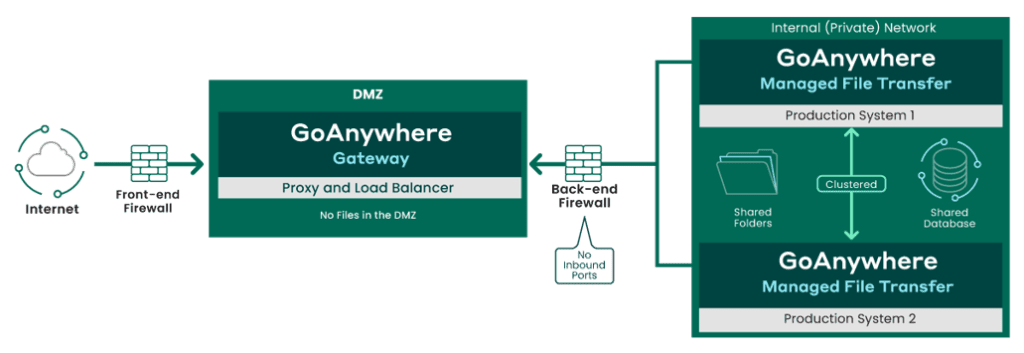
GoAnywhere Gateway is an enhanced reverse and forward proxy that provides organisations with an additional layer of security for exchanging sensitive data with trading partners.
With Gateway, file sharing services can be kept safely inside your private network, without exposing sensitive data to your DMZ (Demilitarised Zone), and connections can be made to external systems on behalf of users in the private network.
With a DMZ secure gateway, like GoAnywhere Gateway, security concerns are solved by allowing an organisation to move file sharing and other public services from the DMZ into the private network without having to open any inbound ports. This approach keeps data files safe in the private network since they no longer need to be staged in the DMZ. It also helps support compliance with PCI DSS, HIPAA, HITECH, SOX, GLBA, and state privacy laws due to the lack of inbound ports needing to be opened into your private network.
GoAnywhere Gateway also supports FTP, FTPS, SFTP, SCP, HTTP, HTTPS, and AS2 file transfer protocols. With Gateway, file sharing services can be kept safe and secure inside your private network, without exposing data to your DMZ.
Reverse and Forward proxy
The reverse proxy handles inbound requests from trading partners, while the forward proxy takes care of outbound file transfer requests from internal employees and systems. Below more technical details!
Reverse Proxy
A reverse proxy is an intermediate connection point that serves as a gateway between users and your origin server. This type of proxy server retrieves files or other resources on behalf of a client. In the case of GoAnywhere Gateway’s reverse proxy, when an external client (trading partner) connects to a listener on GoAnywhere Gateway in the DMZ, GoAnywhere Gateway will make a request over the control channel to GoAnywhere MFT in the private/internal network. GoAnywhere MFT will then create a new outbound data channel to GoAnywhere Gateway. This data channel will be attached to the desired service (e.g. FTP, FTPS, SFTP, HTTP/s) and all traffic for that session will be routed over this new data channel including client authentication requests, data and commands. When the session is terminated, the corresponding data channel will be removed.
Forward Proxy
Similar to a reverse proxy, a forward proxy also serves as an intermediary between clients and servers; however, forward proxies filter connections going out (where reverse proxies filter connections coming in) from the internet to your servers.
The Forward Proxy in GoAnywhere Gateway allows you to route client requests from GoAnywhere MFT (in the private/internal network) to external FTP, FTPS, SFTP and SCP servers without revealing the identity or locations of your internal systems. The Forward Proxy is additionally used by GoAnywhere MFT to route active and passive FTP and FTPS data connections through GoAnywhere Gateway.
When a process in GoAnywhere MFT needs to make an outbound connection through the proxy, a request is made to GoAnywhere Gateway with the address of the intended destination. GoAnywhere Gateway will then establish the connection to that destination and will bridge it to the requesting system.
Migration XFB Gateway for a PeSIT use
Discover how our super experts proceeded for this customer solution replacement.
PCI DSS about DMZ requirements
GoAnywhere Gateway is an important security component for protecting cardholder data and helping organisations to comply with PCI DSS. By allowing organisations to keep sensitive files and credentials out of the DMZ (demilitarised zone) while not requiring inbound ports to be opened into the internal network, GoAnywhere Gateway is specifically useful for meeting the requirements of PCI DSS:
1.3 Prohibit direct public access between the Internet and any system component in the cardholder data environment.
1.3.1Implement a DMZ to limit inbound traffic to only system components that provide authorized publicly accessible services, protocols, and ports.
1.3.2 Limit inbound Internet traffic to IP addresses within the DMZ.
1.3.3 Do not allow any direct connections inbound or outbound for traffic between the Internet and the cardholder data environment.
1.3.4 Implement anti-spoofing measures to detect and block forged source IP addresses from entering the network.
1.3.5 Do not allow unauthorized outbound traffic from the cardholder data environment to the Internet.
1.3.6 Implement stateful inspection, also known as dynamic packet filtering. (That is, only “established” connections are allowed into the network.)
1.3.7 Place system components that store cardholder data (such as a database) in an internal network zone, segregated from the DMZ and other untrusted networks.
1.3.8 Do not disclose private IP addresses and routing information to unauthorised parties. Note: Methods to obscure IP addressing may include, but are not limited to:
- Network Address Translation (NAT),
- Placing servers containing cardholder data behind proxy servers/firewalls or content caches,
- Removal or filtering of route advertisements for private networks that employ registered addressing,
Want to know more about gateway?
How BlueFinch-ESBD can help you to create your MFT experience?
Have a 15 minutes chat with our MFT expert. Quick and easy on 1 click! 😁